In an era where digital privacy is paramount, recent findings have unveiled a concerning vulnerability within Apple’s Find My network that invites scrutiny and caution. Researchers from George Mason University have discovered that this network can be exploited to inaccurately track the location of any Bluetooth device, including Android phones and gaming consoles, by misleading the system into mistaking them for AirTags. This alarming flaw not only highlights the potential for malicious tracking but also emphasizes the importance of being vigilant about app permissions. As we delve into the details of this exploit, it becomes crucial for users to understand the implications and protect their devices from unwanted surveillance.
| Attribute | Details |
|---|---|
| Vulnerability Name | nRootTag |
| Discoverer | Researchers from George Mason University |
| Affected Devices | Any Bluetooth device, including Android phones, Smart TVs, gaming consoles, VR headsets |
| Tracking Range | Within 10 feet |
| Success Rate | 90% |
| Access Requirements | No admin-level access required |
| Potential Risks | Stalking and unauthorized tracking of devices |
| Recommendations for Users | Be cautious of apps requesting unnecessary Bluetooth permissions; keep device software updated |
| Apple’s Response | Vulnerability reported in July 2024; no fix implemented yet |
Understanding Apple’s Find My Network
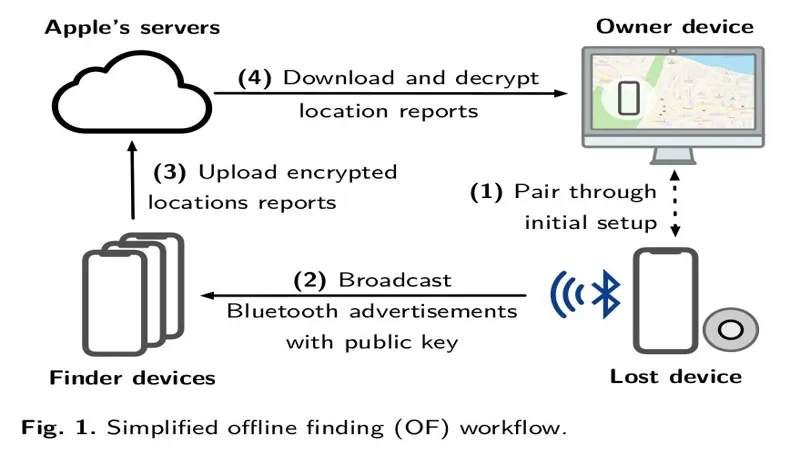
Apple’s Find My network is a helpful tool that lets you find lost devices like iPhones and AirTags. It uses Bluetooth technology to connect to nearby devices, making it easier to track their locations. If you’ve ever misplaced your phone, this feature can be a lifesaver! However, it’s important to understand how it works and what risks come with it, especially regarding privacy and security.
While Find My network is designed to help users, it can also be misused. Some people have taken advantage of this technology to track others without their consent. This raises major concerns about privacy, as it can lead to unwanted surveillance. Apple has worked hard to put safety measures in place, but new vulnerabilities still emerge, reminding us to stay vigilant when using these tools.
The nRootTag Vulnerability Explained
Recently, researchers discovered a vulnerability known as nRootTag that affects Apple’s Find My network. This flaw allows hackers to trick the system into thinking that any Bluetooth device, such as an Android phone or gaming console, is actually an AirTag. This means that, without the owner’s knowledge, someone could track the device’s location very accurately. This discovery highlights a serious flaw in a system that many people rely on.
The nRootTag vulnerability is concerning because it does not require special permissions to exploit. This means that even someone without advanced technical skills could potentially track devices. The researchers found that this exploit works on a wide range of Bluetooth-enabled devices, making it a significant threat. It’s crucial for users to be aware of such vulnerabilities and to take steps to protect their devices.
The Risks of Bluetooth Permissions
Bluetooth permissions are necessary for devices to connect and interact, but they can also pose risks if misused. Some apps ask for Bluetooth permissions that they don’t really need, which can lead to privacy issues. Users should always review the permissions an app requests and be cautious before granting access. This is especially important considering the nRootTag vulnerability, which could potentially exploit these permissions.
To protect yourself, it’s a good idea to only download apps from trusted sources and to regularly check your device’s Bluetooth settings. If an app is asking for permissions that seem unnecessary, think twice before allowing access. By being mindful of the permissions you grant, you can help keep your devices safe from potential threats like the nRootTag vulnerability.
Staying Safe While Using Bluetooth
To keep your devices safe when using Bluetooth, it’s vital to stay informed and take precautions. Always make sure your software is up to date, as updates often include important security fixes. Additionally, consider turning off Bluetooth when you’re not using it. This simple action can reduce the chances of someone exploiting vulnerabilities like nRootTag to track your device.
Moreover, be wary of connecting to unknown devices or public networks. If you receive requests to pair with unfamiliar devices, it’s best to decline. By being proactive and cautious, you can enjoy the convenience of Bluetooth technology while minimizing risks. Remember, staying safe is not just about having the latest gadgets, but also about knowing how to use them securely.
Apple’s Response to Security Vulnerabilities
When vulnerabilities like nRootTag are discovered, it’s important for companies like Apple to respond quickly. Apple has been informed about this issue, and users are hopeful that the company will take the necessary steps to fix it. Addressing such vulnerabilities not only protects individual users but also helps maintain trust in the brand. It’s essential for tech companies to prioritize user safety in their products.
As users, we should also voice our concerns and encourage companies to improve their security measures. Feedback from customers can drive change and lead to safer technology. Until a solution is provided, it’s wise for users to remain vigilant about their device’s security and to stay informed about potential risks. Keeping communication open between users and companies is key to enhancing safety.
The Importance of User Awareness
User awareness is crucial in today’s digital world. Understanding how devices work and the risks involved can empower users to take control of their security. With new vulnerabilities emerging, like nRootTag, being informed helps people make better decisions about their technology use. Knowledge is power, and when users understand the implications of their actions, they can better protect themselves.
Educating ourselves about potential threats and how to mitigate them can significantly reduce risks. Simple practices, such as reviewing app permissions and staying updated on security news, can make a big difference. Encouraging discussions about security within our communities can also raise awareness and help everyone stay safe. Together, we can create a safer digital environment for all.
Frequently Asked Questions
What is Apple’s Find My network?
Apple’s Find My network helps track lost devices like iPhones and Macs using AirTags. However, it can also be misused to track other Bluetooth devices.
How can my Bluetooth device be tracked using Find My?
A flaw in Find My allows hackers to disguise any Bluetooth device as an AirTag, enabling them to track its location without permission.
What types of devices are affected by this tracking vulnerability?
The vulnerability affects various devices, including Android phones, gaming consoles, Smart TVs, and any Bluetooth-enabled device running Linux or Windows.
What is the nRootTag vulnerability?
nRootTag is an exploit that tricks Apple’s Find My network into identifying any Bluetooth device as an AirTag, allowing location tracking without the owner’s knowledge.
How accurate is the tracking with this exploit?
The nRootTag vulnerability can pinpoint a device’s location within 10 feet, making it highly effective for tracking stationary devices.
What should I do to protect my Bluetooth devices?
Be cautious of apps asking for unnecessary Bluetooth permissions and keep your device software updated to minimize risks.
Has Apple fixed this vulnerability?
As of now, Apple has not yet addressed the nRootTag vulnerability, despite being informed by researchers in July 2024.
Summary
A recent discovery reveals that Apple’s Find My network has a security flaw that allows hackers to track any Bluetooth device, including Android phones. Researchers from George Mason University found that this exploit, named nRootTag, tricks the network into thinking a Bluetooth device is an AirTag, enabling precise location tracking without the owner’s knowledge. The vulnerability affects various devices, including Smart TVs and gaming consoles, and does not require special access. Users are advised to be cautious with apps asking for Bluetooth permissions and to keep their devices updated until Apple fixes the issue.